TL;DR
sudo rm -rf /* # can't have problems without a system
TL;DR
sudo rm -rf /* # can't have problems without a system
Copy. Paste. Enter.
System administrators hate this trick!
Ok, this is a very good cheat sheet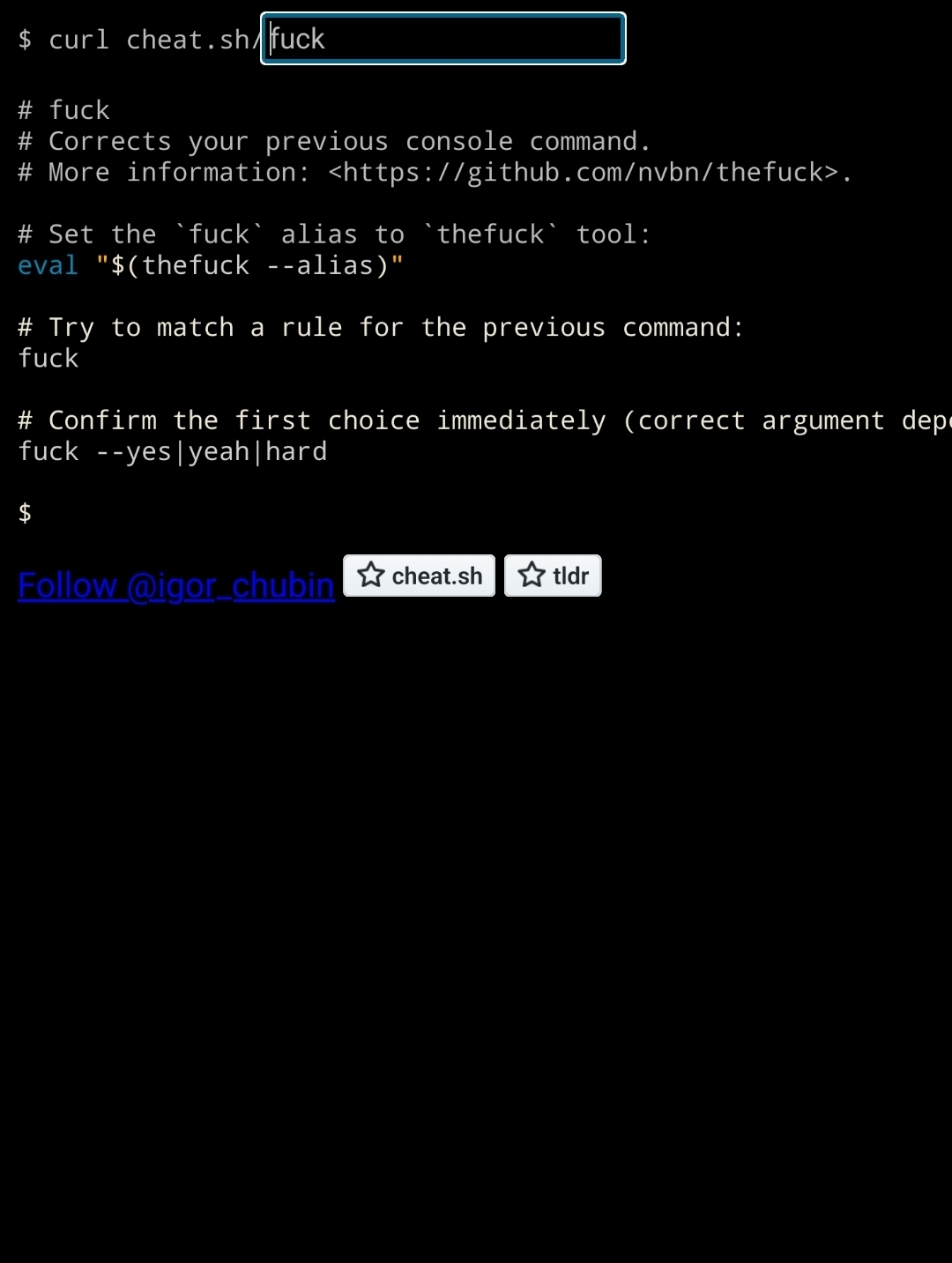
Thefuck is a cool program, but I stopped using it because it was slow.
I haven't had as much luck with that program as I'd like to. :(
My .bash_history using this program...
cheat() {
curl cht.sh/$1
}
Awesome!
sites like this are neat until you remember that curl's willingness to write ansi escape codes to stdout when it is a tty (as this site relies on to format the output when the user agent is curl) is actually a security vulnerability.
Could you give me an ELI5 please
This post The Terminal Escapes: Engineering unexpected execution from command line interfaces has a summary of the longer paper in the first link.
tldr: There are a variety of ways that attackers can cause you to execute execute arbitrary code when you echo their maliciously-crafted data to your terminal. Therefore, when you run curl without redirecting its output, or when you cat a file you've downloaded, you're trusting the server (and also the network, when you don't have https:// in the url) not to exploit you.
Ah ok that makes sense, thank you!
I'm more-inclined to blame a virtual terminal than the program writing the sequences if there's an exploit there.
Of course the terminal emulators are ultimately to blame but when there are so many problems in so many of them, imo curl's default behavior should be to filter its output when writing to a tty.
is there a curl argument that can be used to block this behavior?
You can redirect curl's output to a file with the -o filename option (or with > filename for shell redirection). But in the case of sites like this which output ansi-escape-formatted data that isn't very useful.
Also, after saving unknown data to a file it's common to look at it with less or perhaps xxd or strings or file ... all of which have had their own CVEs in recent years 🤦
Computer security is a fractal of bad news.
Appears to be the same developer as wttr.in
IIRC this site uses TLDR pages
From Wikipedia, the free encyclopedia
Linux is a family of open source Unix-like operating systems based on the Linux kernel, an operating system kernel first released on September 17, 1991 by Linus Torvalds. Linux is typically packaged in a Linux distribution (or distro for short).
Distributions include the Linux kernel and supporting system software and libraries, many of which are provided by the GNU Project. Many Linux distributions use the word "Linux" in their name, but the Free Software Foundation uses the name GNU/Linux to emphasize the importance of GNU software, causing some controversy.
Community icon by Alpár-Etele Méder, licensed under CC BY 3.0